The Calculator Project In Python
Check my cyber securityProjects


I am an ambitious cybersecurity graduate with hands-on experience in AWS. My current focus is on enhancing my defensive security skills through TryHackMe. My passion for SOC and cloud security, combined with my ongoing studies, positions me well for opportunities in SOC as well as AWS security.


Since 2021, I've been hands-on with TryHackMe, diving into Linux systems, SoC analysis, and PowerShell. I learned about Linux, explored blue team tasks , and PowerShell commands to look for bugs in other systems.

HomeHA
facilitating virtual communication for client to stay connected.
Providing tech support for electronic devices and software applications.

IN LSAMP Research Scholar
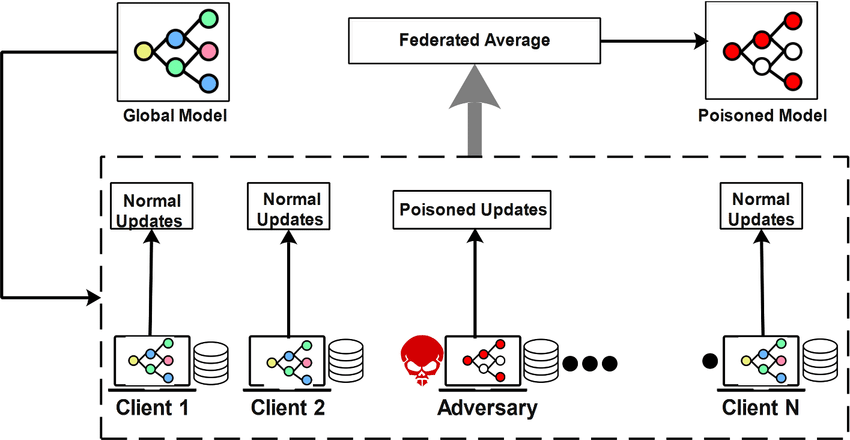
Outlined abstract and research description of federated learning project
Designed and coded traditional federated learning and local attack model algorithm

Learning Assistant
Completed major relating courses, projects from TryHackMe
Assisted LSAMP students who need assistance with course works

General Secretary
Facilitated weekly engagements in addition of a monthly, semi-annual, and annual meetings.
Kept records of meetings, communication and correspondence through phone and email

Analyzed and mitigated real-world different attack scenarios using Cyber range.

Analyzed security events and logs using QRadar

Pursing Informatics with the plan to attend the Cybersecurity graduate program

GPA: 3.66 | Dean’s List: Three semesters
National Science Foundation: LiFT Scholar
LSAMP (Louis Stokes Alliances for Minority Participation) Scholar

Received cybersecurity training with an immersive experience that simulates a real-world SOC and leverages real-world security and network infrastructure.
Utilized commercially security products, while a sophisticated attack generator runs a wide range of attacks
Check my cyber securityProjects
Check out my portfoliolet me know if you have SOC role .,
Library Management


In the ever-expanding landscape of technology, one topic has taken center stage like never before: cybersecurity. It’s not just a buzzword; it’s a critical necessity that has garnered global attention. From Hollywood blockbusters to gripping documentaries, the world has witnessed the captivating drama of cybersecurity unfold in front of our eyes. In this blog, we’ll delve into the famous aspects of cybersecurity that have captivated minds worldwide.
**1. The Great Data Heist – Not Just Hollywood Fantasy:
Remember those edge-of-your-seat moments in movies where hackers breach impenetrable fortresses of data? The scary part is, it’s not just fiction. Real-world data breaches, like the infamous Equifax breach, have exposed millions of individuals’ sensitive information, revealing that truth can sometimes be more dramatic than fiction.
**2. Ransomware: A Digital Hostage Situation:
The ransomware phenomenon has not only gripped IT departments but also found its way into pop culture. High-stakes television shows have depicted the nail-biting tension of ransomware attacks, where institutions, municipalities, and even hospitals fall prey to digital hostage-takers. The WannaCry and NotPetya attacks serve as real-world examples that demonstrate the far-reaching impacts of such cyber assaults.
**3. The Rise of Ethical Hackers – The “Good” Cyber Warriors:
In a world where cybercriminals hold digital weapons, ethical hackers have risen to counteract their influence. The concept of hacking for good, often glamorized in films and documentaries, has led to the emergence of a new breed of cyber warriors. These white-hat hackers work to uncover vulnerabilities, strengthen defenses, and safeguard our digital world.
**4. Cyber Espionage: State-Sponsored Intrigue:
From alleged election interference to large-scale data theft, the arena of cyber espionage has become a real-life espionage thriller. Nation-states have been accused of using cyber tools to infiltrate rival nations’ networks, and the intrigue surrounding these activities has captured the world’s attention, blurring the lines between traditional warfare and digital conflict.
**5. Dark Web Chronicles – Where Shadows Thrive:
The dark web, a hidden part of the internet, has long been a topic of fascination and fear. Documentaries and exposés have unveiled its sinister secrets, highlighting the sale of stolen data, illegal goods, and cybercriminal services. The intrigue surrounding the dark web serves as a stark reminder of the dual nature of technology – a tool for both progress and malevolence.
Conclusion:
Cybersecurity has transcended its status as a niche topic, infiltrating popular culture and public consciousness. It’s not just an IT concern; it’s a global imperative. The stories of cyber espionage, data breaches, and ethical hackers have become the stuff of legends, illustrating the power of technology to shape our lives in ways we never imagined. As we navigate the digital realm, it’s essential to be aware, informed, and prepared – because in the realm of cybersecurity, truth can indeed be stranger than fiction.

In an era dominated by technology, cybersecurity is non-negotiable. Here’s a concise handbook to fortify your digital defenses:
1. Fort Knox Passwords: Craft strong, diverse passwords; double up with two-factor authentication.
2. Update Diligently: Regularly update devices and software to plug security gaps.
3. Digital Guardians: Employ reputable antivirus and firewall programs.
4. Network Smarts: Prioritize encrypted connections and shun public Wi-Fi for sensitive dealings.
5. Street Smart Online: Train your radar for phishing and social engineering ploys.
6. Data Insurance: Routinely back up data to thwart potential loss.
7. Access Code: Restrict data access to only those who truly need it.
8. Game Plan Ready: Develop a swift-response plan for potential cyber incidents.
In unity, we can erect an unbreachable digital shield.

In our digital world, cybersecurity is paramount. Here’s a concise guide to stay safe:
By working together, we can build a safer digital realm.

Get in touch with me if you have exciting Cybersecurity SOC Analyst opportunities or need personalized guidance on your Cybersecurity academic plan. Let's collaborate to secure the digital realm and shape your path in this dynamic field.
Phone: (317)-954-9044 Email: ssibhatu@iu.eduCopyright Samuel Sibhatu